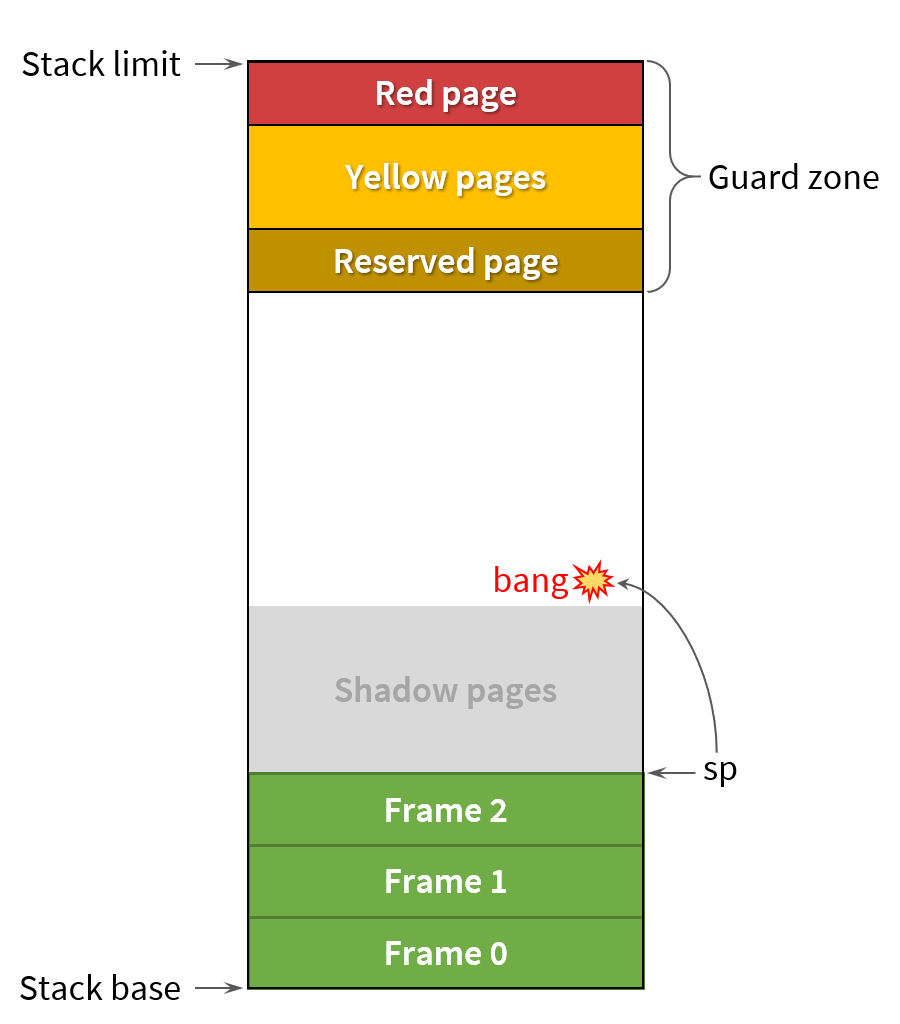
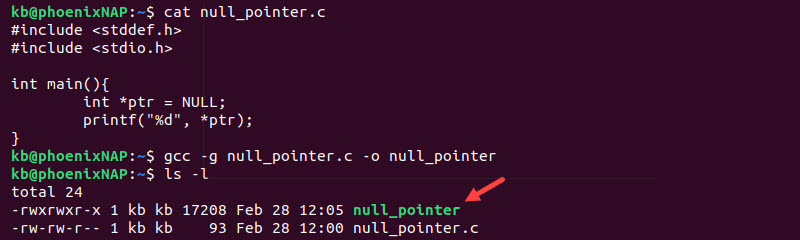
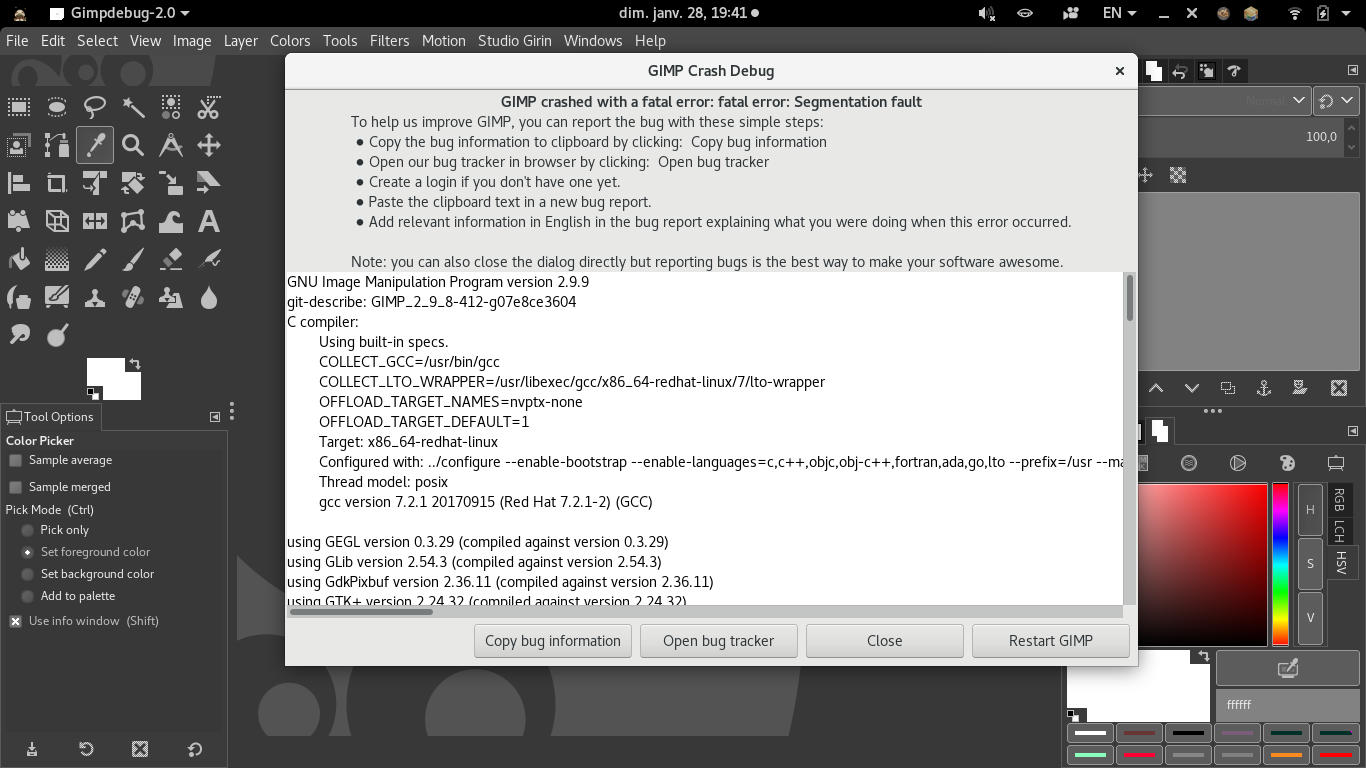
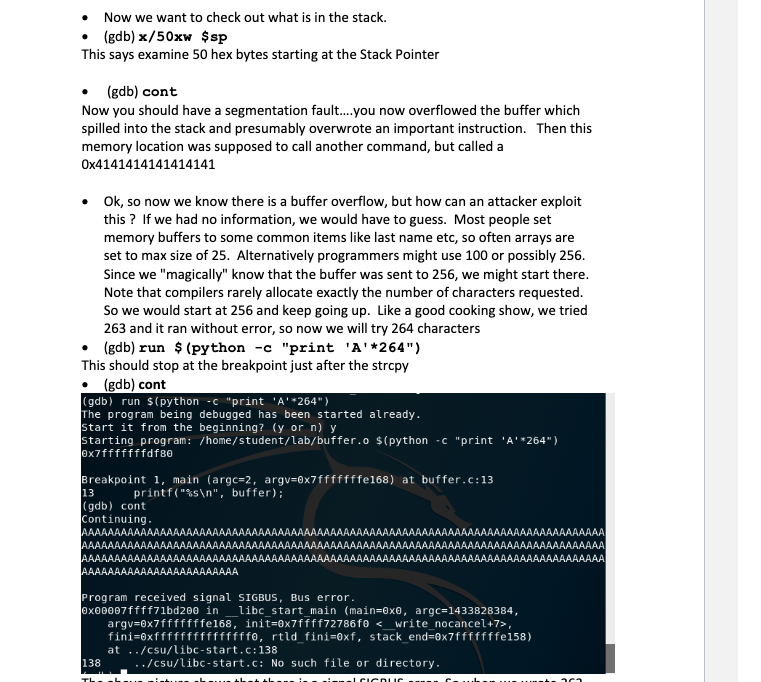
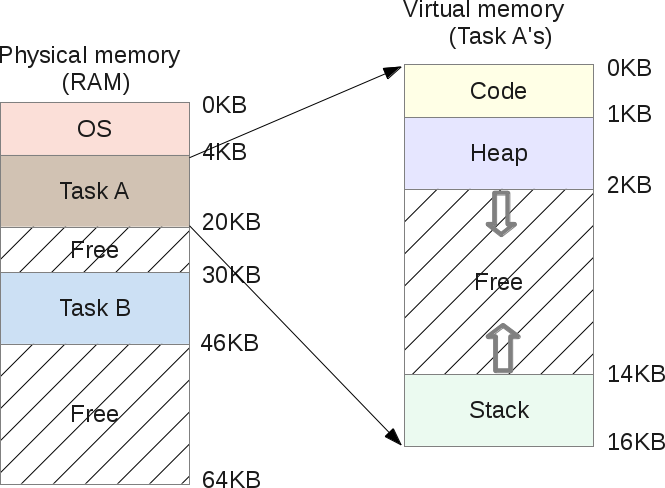
Stack Smashing Failures (SIGSEGV) instead of NullReferenceExceptions · Issue #12891 · dotnet/runtime · GitHub

Shellcode throws sigsegv after changing return pointer with a format string vulnerability in 32-bit application running on 64-bit os : r/LiveOverflow

warning messages - What does Segmentation fault (core dumped) actually mean? - Mathematica Stack Exchange
Shellcode throws sigsegv after changing return pointer with a format string vulnerability in 32-bit application running on 64-bit os : r/LiveOverflow
Segmentation Fault when running stack in zsh (MacOS) · Issue #5607 · commercialhaskell/stack · GitHub

Shellcode throws sigsegv after changing return pointer with a format string vulnerability in 32-bit application running on 64-bit os : r/LiveOverflow